SOC2 Compliance: A Product Leader’s Guide to Getting It
Here at ProdPad, we’ve worked hard to achieve our SOC2 compliance and maintain the standards it promotes. It was a journey well worth taking, to reassure our prospective and existing customers that they’re in safe hands.
It’s no secret that data breaches and cybersecurity threats loom large these days, and maintaining the integrity and confidentiality of your customer data has never been more important. That’s where SOC2, an auditing procedure developed by the American Institute of CPAs (AICPA), comes in. It’s a pivotal standard for any tech or service-oriented company.
Having been through the work involved to secure SOC2 compliance, I’m here to share what we learned and help you do the same!
What is SOC2?
SOC2 is designed to ensure that you securely manage your data to protect both your organization’s interests and your clients’ privacy. It’s particularly relevant for businesses that use cloud technology to store customer information, making it a really useful benchmark for SaaS companies and cloud vendors alike.
The SOC2 framework is structured around five Trust Service Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. Each of these criteria addresses a different aspect of operational security and data management:
In this article, I’ll take you through:
- Why SOC2 compliance is important
- The three main components of SOC2
- Why it’s a useful starting point for your compliance journey
- How to become SOC2 compliant
What makes SOC2 compliance so important?
Essentially, SOC2 is all about safeguarding data and building trust. If you’re handling sensitive information (and let’s face it, pretty much all information is sensitive these days), achieving SOC2 compliance isn’t just about meeting a regulatory benchmark. It’s a clear way to demonstrate that your company is serious about security.
Given how concerns over data privacy are escalating, being SOC2 compliant can provide you with a competitive edge. It shows you’re a trustworthy and secure partner to work with. This is getting more and more important, especially as potential enterprise customers and partners often require SOC2 compliance as a prerequisite for engagement.
Something that makes SOC2 stand out is its adaptability – you’re not required to meet all five of the criteria it’s judged on, but can choose those relevant to your business operations and objectives. This flexibility lets you tailor your compliance efforts to what’s applicable to your product, rather than adopting a less efficient one-size-fits-all approach.
SOC2 also allows you to design your controls to meet the particular TSC requirements that you pick, unlike other compliance standards that offer a prescriptive list of controls. This customizability makes SOC2 a versatile and appealing option, especially for those of us working with SaaS and cloud services.
SOC2 compliance is a big win for any organization that stores or processes customer data. By adhering to the SOC2 framework and achieving compliance, you’ll both protect your clients and your business from data breaches and cyber threats, and also enhance your marketability, and build stronger trust with your customers and partners.
Trust Service Criteria, controls, and evidence: the pillars of SOC2 compliance
The Trust Service Criteria (TSC), controls, and evidence are the bones of SOC2’s framework. This framework helps you prove that your company is dedicated to protecting customer data through a structured and transparent approach.
What are the Trust Service Criteria (TSC)?
The TSC are a set of principles that underpin SOC2 compliance, providing a comprehensive blueprint for organizations to manage customer data securely and responsibly.
By adhering to these criteria, you can align your practices with best-in-class security standards, protecting sensitive information from being spread.
The five TSC are:
- Security: Serves as the baseline criterion, emphasizing the need for robust access controls, firewalls, intrusion detection, and other preventative measures to safeguard system resources. It’s the only mandatory principle, underscoring its importance in the SOC2 framework.
- Availability: Targets the reliability of services, requiring systems to be accessible and operational for users as agreed upon in SLAs or contracts.
- Processing Integrity: Focuses on ensuring that system processing is accurate, timely, complete, and authorized, underpinning the reliability of operational processes.
- Confidentiality: This concerns the protection of confidential information from unauthorized access and disclosures, applying primarily to data that is restricted to certain users or organizations.
- Privacy: Relates to the handling of personal information in accordance with the company’s privacy notice and applicable privacy regulations, ensuring the ethical management of personal data.
What role do controls play in SOC2 compliance?
Controls are the specific practices and policies that are put in place to meet your chosen TSC. They are the mechanisms you use to put those criteria in operation, and cover everything from meatspace security measures to digital safeguards and procedural protocols.
Your controls will need to be designed around the unique risks and operational environment that you’re working with, and the specific TSC you’re aiming to comply with. Using this bespoke approach will let you address your specific security and compliance needs more efficiently and effectively, and help to embed SOC2 principles into your operational DNA.
Examples of SOC2 controls
Here are a few examples of the sort of controls you might need to implement:
- multi-factor authentication for system access
- encryption of data in transit and at rest
- regular vulnerability assessments
- employee training programs on data protection
How do you use evidence to demonstrate your SOC2 compliance?
There’s no point going through all that hard work and not having anything to show for it. That’s why evidence collection is such a critical component of the SOC2 compliance process – you must document and demonstrate the effectiveness of your controls.
This involves gathering, organizing, and presenting data that proves that you’re adhering to the TSC through the controls you’ve implemented. It plays a crucial role during the final SOC2 audit, as the auditors will review this evidence to assess the organization’s compliance with the selected TSC.
Examples of SOC2 evidence
The evidence you’ll need to gather for your SOC2 audit includes things like:
- policy documents
- system logs
- audit trails
- incident response records
- employee training records
Collecting and managing your evidence is an ongoing process. You need to continuously monitor and adjust your controls as the playing field changes. After all, hackers never stop iterating, so neither can you.
Why is SOC2 a good place to start?
Thanks to its flexibility compared to other compliance standards, SOC2 is a particularly good fit if you’re at the start of your business’ compliance journey, especially for startups and smaller companies. By letting you choose specific TSC that match your needs, it gives you a tailored compliance path that will align more closely with your company’s risk profile and operational priorities.
The initial focus on the mandatory Security criterion gives you a solid foundation to build from, and lets you add to it when you need to and are ready to. It accommodates business growth, allowing you to phase your compliance process, and provides scalability. This is really useful for rapidly evolving startups and smaller businesses, providing a baseline to build upon with additional compliance layers as they grow.
Compared to more prescriptive standards like ISO27017 and ISO27018, SOC2’s less stringent approach gives room for greater innovation and agility in meeting the compliance requirements, so you’ll have the freedom to design controls that fit how your business and product work.
SOC2’s model encourages a customized, scalable approach to compliance, focusing on security while enabling you to adapt and evolve your compliance strategy as your business grows. Embracing its adaptable framework, will help you make sure that you’re on top of security and privacy now, and in the future.
When you’re ready to start thinking about your next compliance goals after SOC2, be sure to check out my full guide on enterprise-ready compliance.
How do you achieve SOC2 compliance?
The journey to SOC2 compliance is a thorough process, to say the least! There are a bunch of critical steps that you’ll want to get prepared for, from the initial selection of Trust Service Criteria (TSC) to the final audit.
By the end of this pathway, you’ll not only meet the stringent requirements set forth by SOC2, but you’ll also enjoy enhanced overall security and operational integrity.
This isn’t the sexiest initiative on your roadmap, nor will it be the most fun you’ve ever had at work, but by heck you’ll feel like celebrating when it’s done and you have that compliance badge in your hand.
So, let’s kick off and explore these steps in detail, highlighting where you, as a product leader, can help your teams navigate this complex landscape.
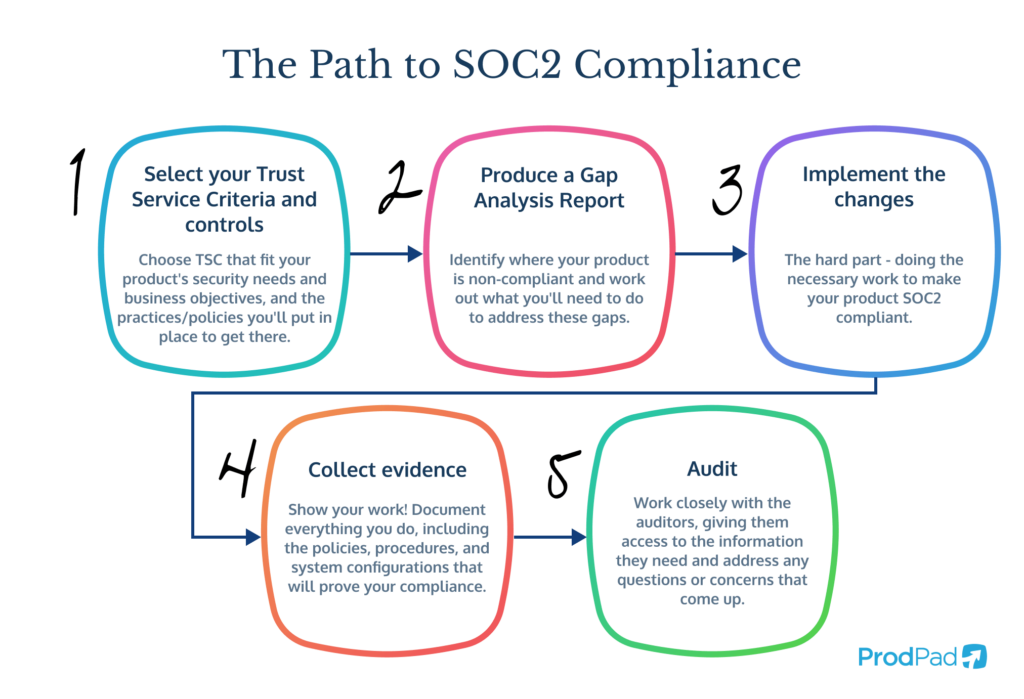
1. Select your Trust Service Criteria and controls
The first step involves deciding which of the TSC you want to be included in the SOC2 audit. This decision defines the scope of your compliance efforts and helps you ensure that you’ve focused on the areas that are most relevant to your business and your customer expectations.
As a Product leader, you will play a key role here, as it’s your job to make sure the selected criteria align with the product’s security needs and business objectives. You’ll need to work closely with a range of internal stakeholders, including security teams and executive management, to identify which TSC fits your needs.
After selecting the relevant TSC, the next stage of the process is designing and implementing controls that meet the criteria. It takes a deep understanding of your product’s architecture and operational workflows to get this stage right, as well as a strategic approach to embedding security into these processes.
2. Producing a Gap Analysis Report
Next, you should conduct a comprehensive gap analysis to compare your current security practices against the SOC2 requirements. This report will highlight where you’re non-compliant, and lays out a framework for addressing these gaps.
You need to make sure that the gap analysis covers all aspects of your product, infrastructure, and company operations, so it can give you a clear picture of the steps you’ll have to take to achieve compliance.
Make sure to engage teams from across the business when reviewing your report. That way you’ll ensure you’re covering all perspectives when you work out what to do about it. The report should offer actionable insights, so you can prioritize your compliance efforts based on risk, impact, and resource availability.
3. Implement the changes
Based on what you discover with your gap analysis, the real work starts, because it’s time to get busy implementing the necessary changes to your policies, procedures, and tech. This can often be the hardest part of the whole process, as you’ll likely find you need to make some pretty significant modifications to how you do things, and your product itself.
It’s also your time to shine, because you’ll be coordinating the changes across all the affected teams. It’s up to you to make sure that everyone’s work aligns with the SOC2 requirements, and doesn’t disrupt the product’s functionality or user experience.
This is your initiative to manage, with a clear schedule, responsibilities, and milestones to guide the implementation process. You’ll want to help and encourage your departments to collaborate, because the changes have to be implemented cohesively across the whole company.
4. Collect your evidence and prepare for the audit
As you are making the necessary changes, it’s vital you start collecting the evidence you’ll need to prove your compliance with the selected TSC and controls. Simply put, there’s no point in doing the work if you can’t show what you’ve done.
Your evidence will be reviewed by the auditors to assess the company’s adherence to SOC2 standards. You need to ensure that evidence is being collected systematically and comprehensively, and that it covers all aspects of the changes you’ve implemented.
Having detailed documentation of all the changes made, including your policies, procedures, and system configurations, is essential for your evidence-collection process. You’ll probably find it helpful to regularly review and update your evidence collection process as you go to ensure that all the necessary documentation stays accurate and up-to-date.
5. Audit
The final step in the SOC2 compliance journey is the audit, conducted by an AICPA-certified auditor. They will assess how effective your controls are and the accuracy of the evidence you’ve provided. You’ll want to work closely with the auditors, giving them access to any information they need and deal with any questions or concerns that may crop up during the audit process.
Giving your support to the auditors, including providing them with clarifications and any additional documentation they need, is key to a successful audit. Plus, after the audit, you should review their findings and implement any recommended improvements.
What are the two types of SOC2 reports?
Using everything I’ve told you so far, you should be able to lay a solid and comprehensive foundation for your journey to SOC2 compliance. And at the end of that journey is the all-important final milestone: your SOC2 report.
This report is a testament to your company’s adherence to the stringent standards set by the AICPA on security, privacy, and data protection. Again, though, SOC adds flexibility to the process by offering two types of SOC2 reports at differing levels of rigor – Type 1 and Type 2.
SOC2 Type 1 report
The SOC2 Type 1 report (also written as Type I) is often seen as the first stage in the SOC2 compliance journey. It provides a snapshot of your organization’s commitment to security and operational integrity.
This report demonstrates your company’s capability to design systems and controls that effectively meet your chosen TSC. It can serve as a powerful tool in the earlier stages of product development or market entry, as it offers reassurance to your stakeholders and customers that you take security seriously.
Gathering and presenting evidence required for a Type 1 report still requires meticulous documentation of how you design your systems and controls, so it will still take thorough planning and organization.
SOC2 Type 2 report
The SOC2 Type 2 report (also written as Type II) goes a step further, as it evaluates the operational effectiveness of those systems and controls over a period of time. This type of report provides a more comprehensive view of how the controls are implemented and function in your daily operations.
It’s a more robust demonstration of your company’s commitment to maintaining high standards of security and privacy, as it shows you can design, effectively implement, and maintain controls that will protect your customer data over time.
Achieving a Type 2 report takes continuous effort, monitoring, adjusting, and documenting the operational effectiveness of your controls, so you’ll really have to commit to constantly updating and improving to maintain compliance.
Example of a SOC2 Type 2 report
If you’re wondering what the eventual report will look like, why not take a look at ours here at ProdPad. You can find details about our SOC2 compliance in our Trust Center and download a copy of the Type 2 report.
How can product leaders help guide the SOC2 compliance process?
For product leaders, getting to grips with SOC2 reports is more than ticking boxes—it’s a strategic journey. Here’s how to tackle it:
Coordination is key: It’s crucial to bring teams from Security, Operations, and Product Development together. As a product leader, you’re the linchpin in this effort, working to build a culture where compliance and security are everyone’s business.
Strategize for success: Aligning your SOC2 compliance with your business goals is essential. Think of it as steering your compliance efforts in a way that fuels innovation and growth, rather than holding them back.
Turn compliance into opportunity: Getting your SOC2 reports isn’t just about meeting standards; it’s a chance to stand out. Use it to underscore your commitment to security and privacy. This is a powerful message for your customers and a solid foundation for growth.
Successfully jumping through all the hoops to get your SOC2 reports, whether Type 1 or Type 2, is a clear signal of your commitment to the highest security and privacy standards. These aren’t just shiny badges to collect. They’re tools that can enhance your product’s appeal, build customer trust, and drive your company forward.
By being smart about how you navigate the SOC2 compliance path, and by making the most of the knowledge the reports can give you, you’re not just securing your data (important as that is!). You’re securing a competitive edge in a world that values security more than ever.
